Difference between revisions of "Main Page"
| Line 1: | Line 1: | ||
| − | '''Socology<br>''' | + | '''Socology<br>'''[[File:socologylogo-white.png]] |
''The study of Security Operations'' | ''The study of Security Operations'' | ||
Revision as of 04:57, 17 October 2018
Socology The study of Security Operations
The study of Security Operations
Consult the User's Guide
for information on how to contribute to this page.
Contents
Objective
The objective of socology is to provide the community with guidelines, frameworks and resources that improve Security Operations from a Management and Strategic level. While the framework can be used to evaluate your own Security Operations Center, this is designed to be a guideline to improve those ratings.
Why create socology?
- Understand the Complexity - Security Operations is a highly complex and multifaceted portion of Cyber Security. We want SOCs to be successful.
- Implementation - Implementing, maturing and maintaining Security Operations goes beyond technology and tools.
- Guidelines - Socology is attempting to identify those dimensions and some guidelines to help you be successful.
- Lessons Leaerned - Lastly, in discussion with our Subject Matter Experts, common pain points and lessons learned have emerged which we feel would benefit the community to
While framework exist for Risk Management, like NIST [1], CMMI [2] and SOC-CMM [3], the Security Operations field has gaps in guidelines and frameworks for implementation. We are working to study, identify and fill in those gaps where possible.
While ITIL is an excellent resource for IT Operations, we argue it has gaps when applied to Security Operations.
Maturity & Development
Security Operations can be described having a hierarchical developmental sequence as well as maturity. We start at an immature level and then mature along multiple dimensions in parallel. It is recommended to be able to evaluate your developmental sequence and maturity.
In the search for how to organize this information, we have identified several different ways to approach it. This includes:
- RAG - Red, Amber, Green
- Development Cycle - The development cycle of Forming, Storming, Norming and Performing is simple and meaningful. Psychologist Bruce Tuckman first came up with the memorable phrase "forming, storming, norming, and performing" in his 1965 article, "Developmental Sequence in Small Groups."[4].
- CMMI - The Capability Model Maturity Index[[5]] is an excellent way to gauge maturity, however for this framework, which will including guidelines and is more qualitative, we are using the Developmental Sequence.
- SOC-CMM - https://soc-cmm.com/ A Continuous Maturity Model for Security Operations
Core Dimensions
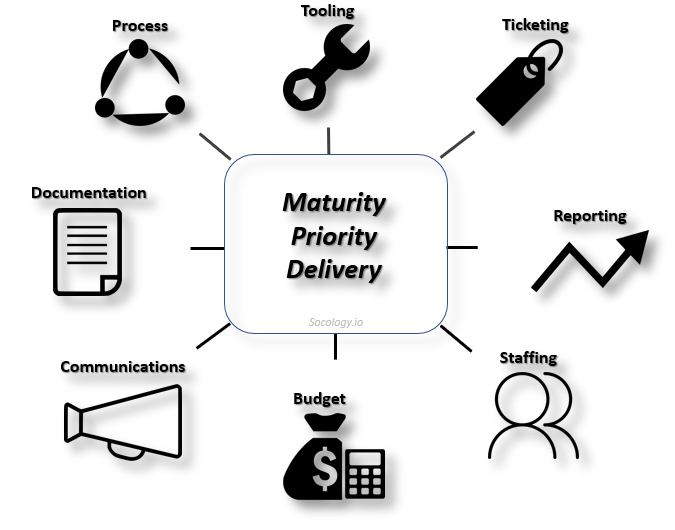
Each Service of Security Operations is broken down into Socology Core Dimensions. Those Core Dimensions are: Process, Tooling, Ticketing, Reporting, Staffing, Budget, Communications and Documentation. This is designed to describe and explore the Service, the Service Management Requirements, the Staffing and Technology at an altitude that allows for flexibility while still providing practical guidance.
The Parts of Security Operations
Click here to view the Parts of Security Operations.
High Level Common Pain Points | Lessons Learned
Context Switching - also discusses Multitasking
Shelfware or Un(der)utilized Tools
Socology Dimensions Map
Click here to view the Socology Dimensions and descriptions.